-
TrackoBit
Manage commercial vehicles with the new-age Fleet Management Software
TrackoBit -
TrackoField
Streamline your scattered workforce with Field Force Management Software
TrackoField -
Features Resources
-
Blog
Carefully curated articles to update you on industrial trends. -
White Paper
Insightful papers and analysis on essential subject matters. -
Glossary
Explore an alphabetical list of relevant industry terms. -
What’s New
Get TrackoBit & TrackoField monthly updates here. -
Case Study
Explore the cases we solved with our diverse solutions. -
Comparisons
Compare platforms, features, and pricing to find your best fit.
-
About Us
Get to know TrackoBit: our team, ethos, values, and vision. -
Careers
Join the most dynamic cult of coders, creatives and changemakers. -
Tech Support
Learn about our technical support team and services in detail. -
Events
Check out the exhibitions where we left our marks and conquered. -
Contact Us
Connect with us and let us know how we can be of service.
How to Prevent Your Connected Fleet From Cyberattacks
- Author:Drishti Dua
- Read Time:7 min
- Published:
- Last Update: December 24, 2025
Table of Contents
Toggle
The fleet business market is all about Connected and Automated Vehicles (CAV) these days. But overexposed automobiles with little to no security implementations are a burden more than an asset to any company.
Table of Contents
Toggle
But we cannot say we are surprised, can we?
It is not like the cybersecurity threat is a new concept. From social media to government databases, everything that has data is a target. Similar is the case with companies using fleet management systems that are responsible for both data collection and storage. It is predicted that 55% of all commercial trucks on the roads will be connected by 2025. Such a huge industry! And an even bigger playground for hackers.
How are Cyberattacks a Threat to Fleet Businesses?
Think the claims we are making are too far-fetched? In Houston, Texas, a pair of hackers managed to steal more than 30 jeeps by exploiting their lock system connected to the internet. Here are some common threats that might put your fleet at risk:
Phishing Attacks
It has been accounted that 80% of all cybersecurity crimes against fleet businesses happened through phishing. Phishing is the act of stealing information by sending a fraudulent message to a person. It contains a message tricking users into revealing sensitive information to the hacker. It can in a way be seen as information theft.
While the motivation behind these attacks can vary, it is safe to say that they greatly affect the operations of any company. In many cases, such sensitive information can be misused to damage fleets to an extent that the business goes under.
Ransomware Attacks
Attacks that end with businesses having to shell out money to keep their privacy and information from being leaked come under this category. The average cost of ransomware attacks has increased to 130,000 dollars by 2020.
Ransomware is when a hacker gains access to the encryption of software. This allows them to change data available in that software and make it illegible for other users. After that, the victim is asked for a ransom to buy back their access to their own software.
Theft
A major threat to any business connected to the internet is theft. This includes stealing both vehicles and consignments. After hacking into a system, a person can access information about all fleet vehicles’ locations. Smart vehicles connected to the same system can also be unlocked and controlled, making theft easier.
Privacy Breach
A privacy breach is the unauthorised use of any personal information by the business. When obtaining information from clients, the business becomes responsible for its safety. But with a failure to do so, not only are they answerable to their customers, but can also lose face.
Leaking information can also lead to exposing a company’s asset valuation and route strategies. This information can be stolen by industry competitors, not only wasting the business’s hard work but also leaving them at a loss of data. Payment details are also vulnerable when a hacker strikes, and the risk of monetary theft is high.
Consequences of Weak Cybersecurity
Now that we are aware of just what threat looms over your business connected to the internet, it is time to see how they affect your fleet operations:
Diminished Profits: Most fleet businesses run with the aim to make profits. But with the breach of privacy comes the threat of losing productivity. No customer wants to entrust their consignments with a business that is unsafe. This can be a major hit to any company’s profitability. Paying ransoms to regain control over software encryption also takes away from their budget.
Low Reputation: As we just mentioned, not safeguarding data can be a loss of confidence for clients associated with a fleet. This can affect their entire clientele and ultimately lead to lost customers.
Unsafe Vehicles: The damage done by cybersecurity threats reaches beyond simple loss of productivity and hindered operation for the business. When a person gains control over a smart vehicle’s controls that are connected to the internet, they can use it to cause physical harm to them as well. It might even endanger the life of a driver!
Data Misuse: Hackers might use the data stolen to sell it to industry competitors. Another scenario might include the hacker posting private information (like vehicle data, and customer details) online. This opens the need for businesses to rebuild their system and opens the gate for other competitors to take them over.
Insurance Claims: When anybody has access to your data, they can very well use it to manipulate information according to their will. Suppose your truck gets into an accident which was not the driver’s fault. You have video telematics proof to claim insurance based on this fact. But somebody deletes this proof, leaving you with no choice but to pay for the accident’s repercussions yourself.
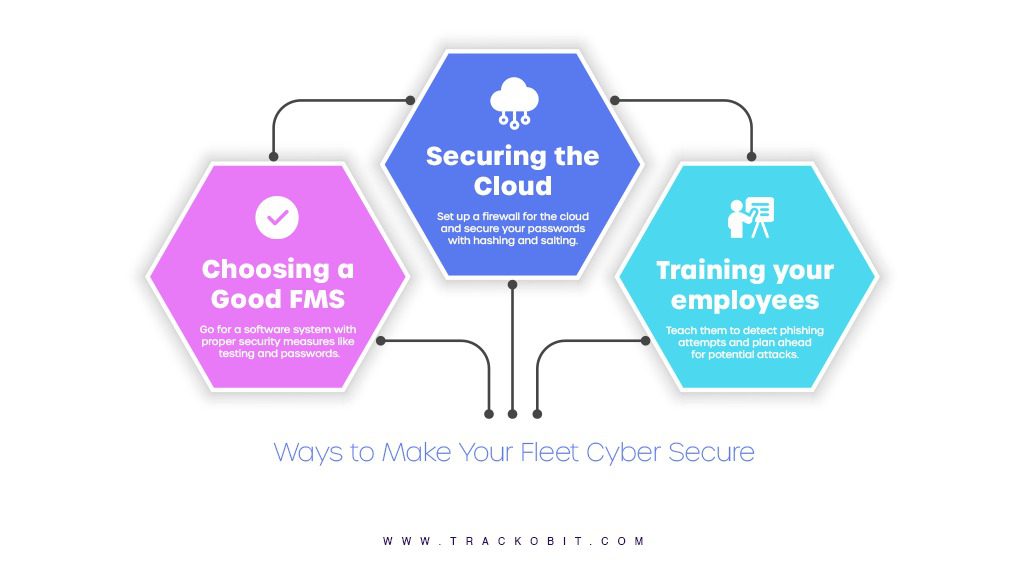
Ways to Minimise Threats of Cyber Attacks Against Your Fleet
Implementing changes to a fleet is probably the last step in making a business safe from cybersecurity threats. Before that, owners need to get to the root of this issue, understanding what gap allows this breach of privacy. And this process is as time-consuming as it is gruelling.
The solution to this problem starts at the very first step of deciding what system you connect your vehicles to in the first place. Let us take a deeper dive into the entire process:
Choosing the Fleet Management Software
How easy is your system to hack into? What is their past safety record like? All these are some reasons you might want to keep in mind while you choose a fleet management system for your fleet. An error at this stage can make all the other steps we are going to discuss ineffectively.
Choosing a responsible software provider goes a long way. They help you tackle many cybersecurity issues right at the base level like:
Include Password Security:Having a system that protects its data with some form of password security, or even an open-source password manager, is very essential. It makes accessing data difficult for unauthorized users. You can also consider using trusted password managers, and look for a 1Password discount to secure your accounts affordably.
Test Software for Loopholes: Ensure that your software providers test their system to detect any potential issue that might cause harm to their clients. This will safeguard your business from upcoming threats.
Update Software Regularly: Cyber threats keep changing over time. With new technological developments, hackers also learn new ways to steal information. This is why it is important that your fleet providers adapt their system to all the newly arising issues.
Allow Customisation: The software should allow you to control how much access you give to your employees. A rigid software will end up putting your company at risk with a standard access plan.
Securing the Cloud
Physical security can be ensured by limiting the access employees might have to your software. But what about the cloud? Is that secure too?
Some measures that help maintain a secure cloud environment are:
Implement Firewalls: This makes it difficult to penetrate through cloud security.
Hashing and Salting Passwords: If a hacker manages to breach through the firewall, this safeguards the password and buys businesses time before their data is poached or manipulated. Both hashing and salting aid the masking of a password, shielding it from being decrypted.
Train Employees
We have mentioned already that limiting access to experts only is an essential part of ensuring fleet safety.
Hmm… But how are experts cultivated?
Through the correct training! This is why it is essential to focus not just on your software but also on the people operating that software.
A business needs to spend time training both managers and drivers to understand the threats they might encounter using a fleet management system. Detecting the early signs of a cyber attack is a preventive measure in itself. A stitch in time saves nine, doesn’t it?
Preventive Training: Training in understanding and detecting potential phishing attempts is very important. Managers should have extensive knowledge so as to not fall prey to such attacks, including using security tools like the best desktop VPN to enhance protection.
Actionable Training: In case the system has been breached already, businesses need to devise a proper plan to deal with such situations in the future. This can include changing passwords, protecting cloud data, and so on. This aids in preventing grave damage to the business by prompt actions.
TrackoBit is the Right Choice
We have already discussed what makes up cyber-safe software. Well, guess what? TrackoBit stands strong on all criteria. With its up-to-date technology, you do not have to worry about regular threats to your company!
The right combination of our system and your capable employees can help maintain a fleet that is both safe and profitable. So why wait? All this is just a couple of clicks away. Request a demo and test out our compatibility with your fleet today.
Drishti Dua, a Content Contributor at TrackoBit has a rich background in literature and professional expertise in SaaS and technology writing. She has carved her niche in the space of Geospatial techn... Read More
Related Blogs
-

5 Best Driver Behavior Monitoring Systems for 2026
Tithi Agarwal February 23, 2026Having the best driver behavior monitoring system is a necessity as it helps you ensure driver safety and optimize operational…
-

Why is Driver Drowsiness Detection System Important for Fleet Management?
Shemanti Ghosh February 4, 2026A driver drowsiness detection system is critical for fleet management. It helps prevent fatigue-related accidents and reduces operational risks through…
-

When Tracking Needs a Clock: Rethinking Fleet Visibility
Tithi Agarwal December 24, 2025Read on to understand why fleet tracking works better when it follows working hours. Because visibility should support operations, not…
-

What Makes TrackoBit’s Video Telematics Software Truly Next-Gen?
Shemanti Ghosh December 17, 2025TrackoBit’s video telematics software blends smart video intelligence with full server control. The result? Superior fleet reliability and safety.

Subscribe for weekly tips to optimize your fleet’s potential!
Your inbox awaits a welcome email. Stay tuned for the latest blog updates & expert insights.
"While you're here, dive into some more reads or grab quick bites from our social platforms!"Stay Updated on tech, telematics and mobility. Don't miss out on the latest in the industry.
We use cookies to enhance and personalize your browsing experience. By continuing to use our website, you agree to our Privacy Policy.